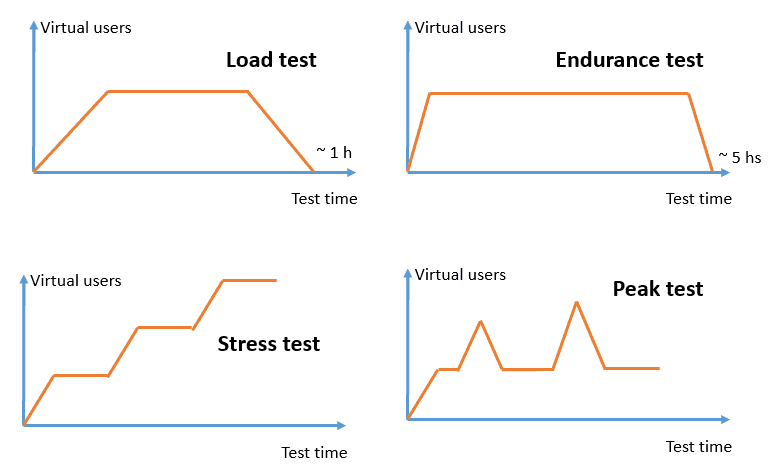
The history of outsourcing is longer than we might think. The first mention of this form of business cooperation dates back to the late 1970s. However, no one will be surprised that before it was written about, it was already used in the USA in the middle of the 20th century.
Outsourcing has transformed over the years and has specialized in specific business areas. Initially, accounting services were most often outsourced, but in our current form, outsourcing has focused on many specific areas.
Today, the market for outsourcing services is very wide and saturated with specialized companies, especially when it comes to the IT industry. On the Polish market, 22% of the IT segment are outsourcing companies, and according to the Central Statistical Office (GUS), 71% of domestic organizations use their services.
Having your own IT department will not provide your company with every specialist. The perfect complement to this can be precisely the contractors from outsourcing. The fact that many companies on the market specialise in this field raises the question, which supplier to choose? What should be the guiding principle when choosing? What aspects to pay attention to? What to avoid when choosing? I will try to answer these and other questions in this article.

Before you start searching, set a goal to achieve with the provider help.
A clearly defined plan or business objective will allow you to determine the role that the outsourcing provider will play in your organization. With the direction you have set, you can explain clearly what you expect from such a partner and how you want them to help you achieve your business goal.
A large corporation or a smaller supplier?
This is another aspect that can cause headaches when choosing a supplier. To make a good choice, it is necessary to determine at the very beginning how we want to cooperate with the supplier. Cooperation with either a large corporation or a smaller supplier has its pros and cons.
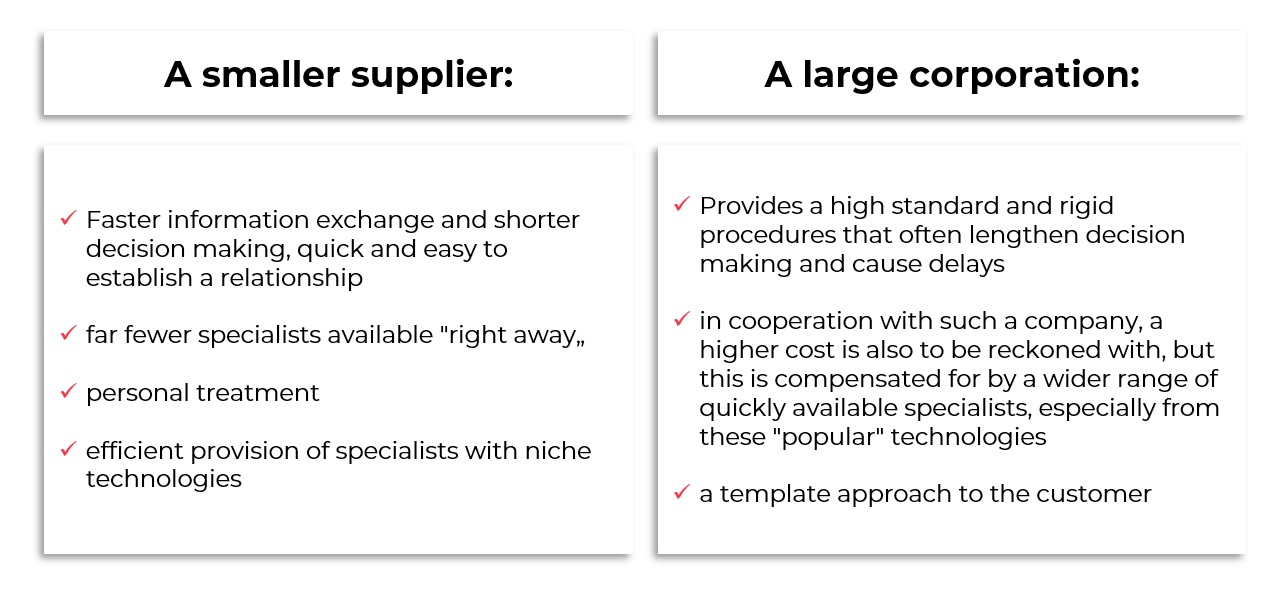
If you are looking for long-term cooperation and know that you will be hiring specialists for longer projects, then a larger supplier will do better. Short annual or semi-annual projects are best done with a smaller partner. A smaller partner will be able to adapt better to the changes and the dynamics of the project.
Check how the company works.
Once you have found several potential outsourcing partners, it is worthwhile to find out what opinions they have and how they work. Pay attention to match the profile of the partner to the project in which they are supposed to help you. Look for companies specialized in a particular field that have experience in implementing projects similar to yours (at least in part). Surely in every case, you will find on the website a case study, recommendations, and completed projects.
However, blind belief in what they write on the Internet can be misleading. It’s worth to go one step further and ask a potential provider for information about the companies who were working with them in the past and call them in person. Then you can ask for a recommendation or short review of the potential provider.
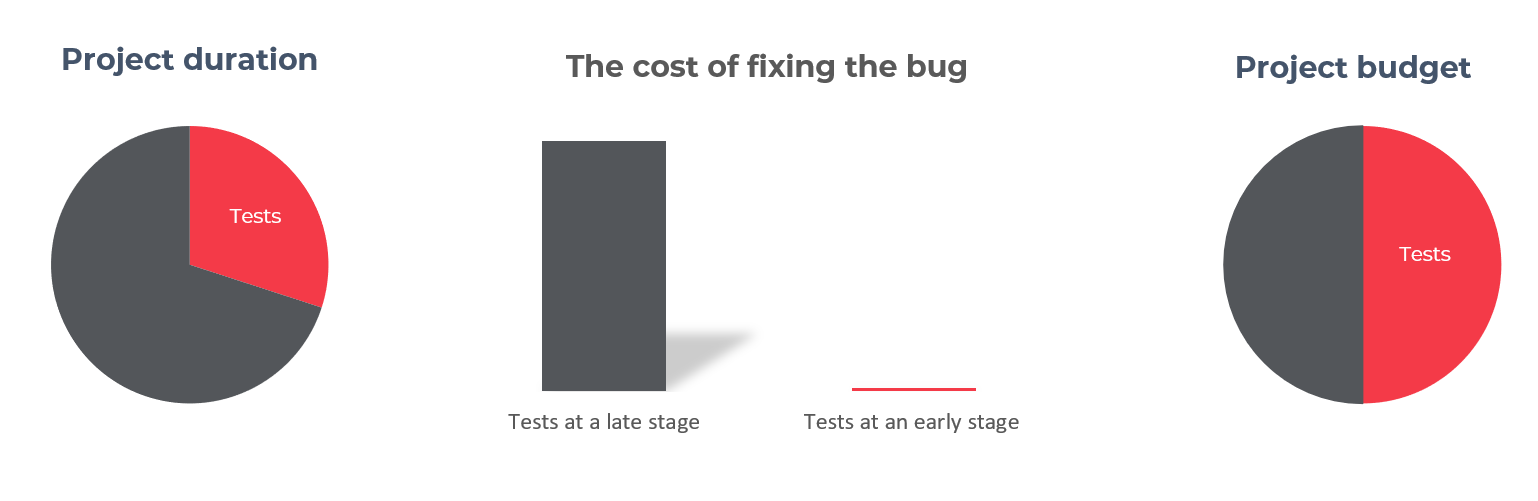
Costs, costs, costs?

I am aware that the costs will dominate the selection of a partner. However, often the lowest costs do not go hand in hand with good quality specialists or cooperation with the supplier itself. Cooperation with a good outsourcing company can bring savings. It is worthwhile to carefully analyze the budget in relation to demand before starting cooperation.
If the project will be settled in the time & material model, it is worth to calculate the exact number of working hours in each month and leave yourself a safety buffer in the form of free funds for possible overtime of specialists. It looks a bit different when the project is paid for in its entirety.
Here we cannot rely only on dry analysis. In such a scenario, it is best to ask the supplier to work for a few test days to get acquainted with the system and perform all the analyses to assess the work and calculate the costs more accurately.
Selection of specialists.
This is the last stage of the supplier search process and the first stage (hopefully beneficial for both parties) of cooperation. Based on the recommended candidates, we choose those with whom we want to work. Before starting any application process, it is important that you calculate how many specialists you need and what skills they should have.








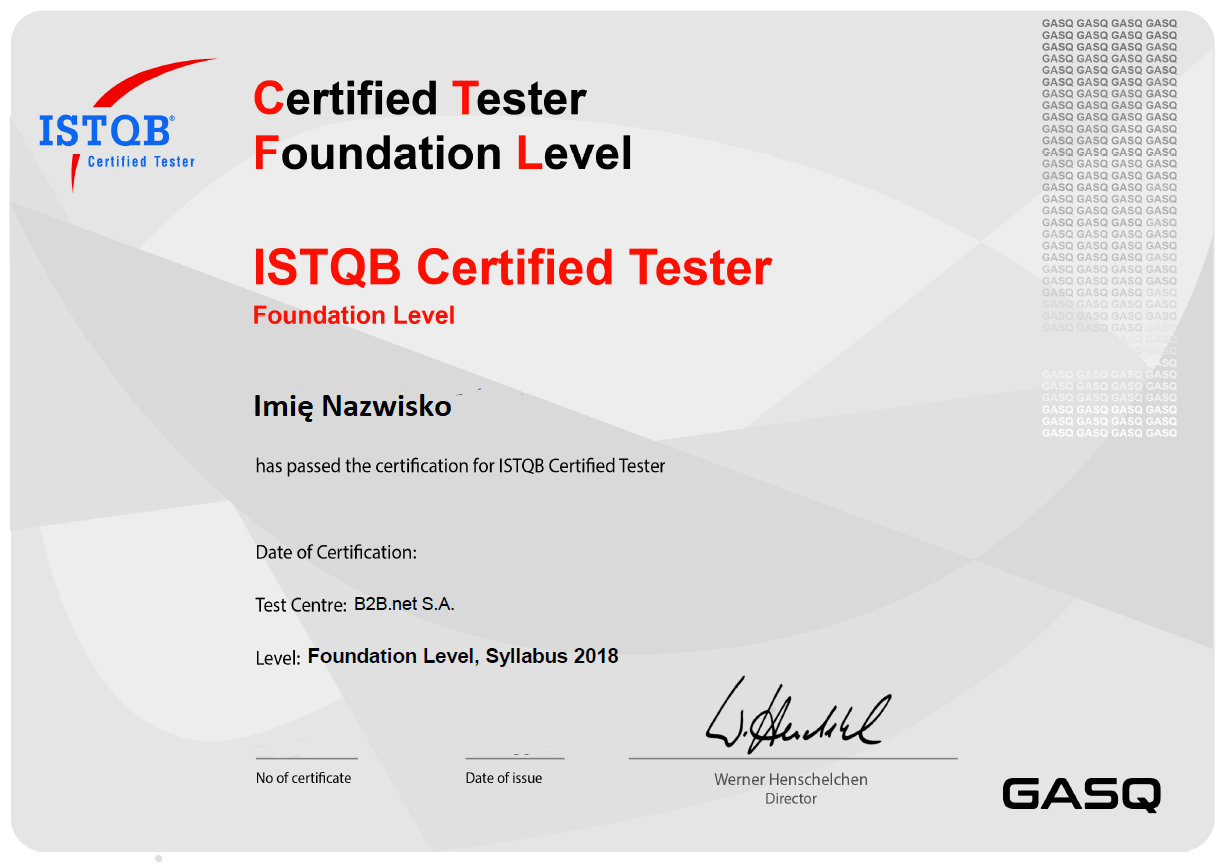 GASQ tells us all the time that they send certificates in up to 8 weeks. Recently they sent it after a week …
GASQ tells us all the time that they send certificates in up to 8 weeks. Recently they sent it after a week …




 ? A desktop computer or laptop with a webcam and microphone
? A desktop computer or laptop with a webcam and microphone ?Google Chrome browser
?Google Chrome browser ? Photo ID
? Photo ID ? Stable Internet connection
? Stable Internet connection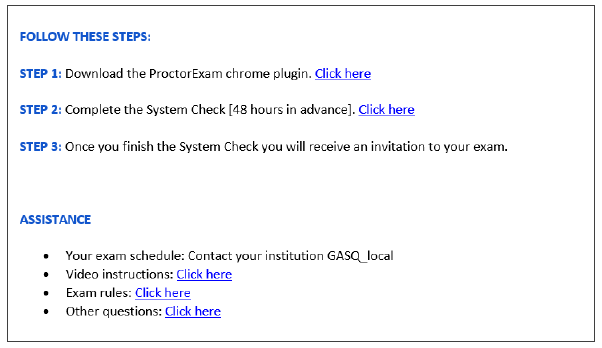
 Mark a question
Mark a question Take notes
Take notes